Data Science & Developer Roadmaps with Chat & Free Learning Resources
SSO
Single Sign-On (SSO) is an authentication process that allows users to access multiple applications or services with a single set of credentials. This streamlined approach enhances user experience by eliminating the need to remember multiple usernames and passwords, thereby reducing the hassle of managing various accounts. SSO works by authenticating the user once through a central Identity Provider (IdP), which then issues a security token that grants access to different services. This not only simplifies the login process but also improves security by minimizing the risk of weak or duplicated passwords across platforms.
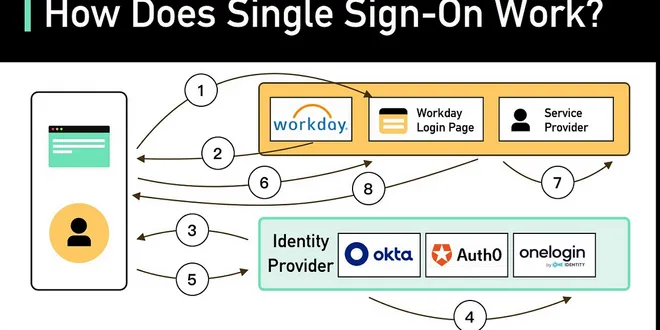
How does SSO Single Sign On Process Works?
Hello guys, In today’s digital landscape, you will often find yourself interacting with multiple applications and services that require authentication. Juggling multiple usernames and passwords can be...
📚 Read more at Javarevisited🔎 Find similar documents

Single Sign-On(SSO) with Spring Boot
There’s a lot of confusion around what SSO and OAuth actually are. Some people think OAuth is a “security thing” and don’t really understand more than that. There is a set of buzzwords that comes when...
📚 Read more at Javarevisited🔎 Find similar documents
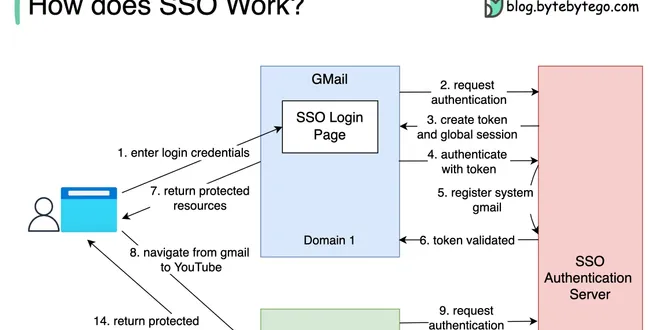
What is SSO (Episode 7)
In this newsletter, we will talk about the following: What is SSO (Single Sign-On)? What is the future of online payments? Top 38 most commonly used programming languages What is IaaS/PaaS/SaaS? What ...
📚 Read more at ByteByteGo Newsletter🔎 Find similar documents
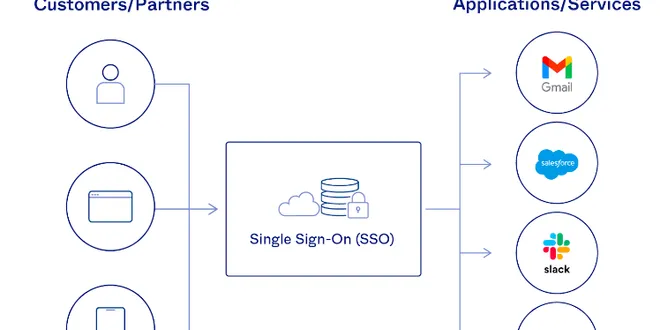
Single Sign-On (SSO): SAML, OAuth2, OIDC simplified
Hello everyone. In this article, we will see about Single Sign-On (SSO) and the 2 protocols which are widely used for SSO namely SAML and OAuth2.This is one of the most complicated areas to understand...
📚 Read more at Javarevisited🔎 Find similar documents
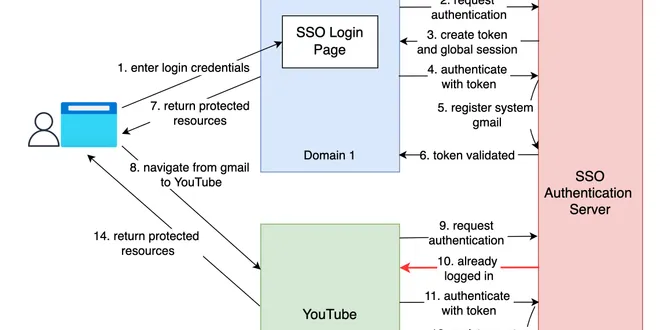
How does SSO Single Sign On Authentication Works?
Hello guys, In today’s digital landscape, you will often find yourself interacting with multiple applications and services that require authentication. Since juggling multiple usernames and passwords ...
📚 Read more at Javarevisited Newsletter🔎 Find similar documents
Single Sign On with Kerberos
I'll explain the Kerberos protocol and browser based Single Sign On authentication with Spnego. Tomcat sequence diagram shows the interactions details.
📚 Read more at Level Up Coding🔎 Find similar documents
Reducing dynamic allocations using SSO/SOO
Dynamic allocations can sometimes cause you other trouble than just throwing when you construct objects despite not having enough memory. They often cost you CPU cycles and can cause memory fragmentat...
📚 Read more at Software Architecture with C plus plus🔎 Find similar documents
Implementing SSO-Based Authentication Between Spring Boot and Angular: A Journey with AWS Cognito…
Implementing SSO-Based Authentication Between Spring Boot and Angular: A Journey with AWS Cognito and Azure AD Hey TechNoir readers, For my first deep-dive tech post, I wanted to tackle something tha...
📚 Read more at Javarevisited🔎 Find similar documents
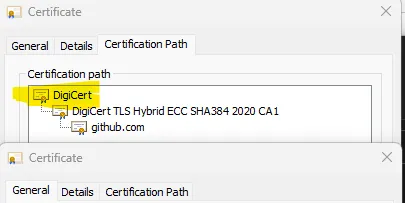
SSL Certificate
Secure Socket Protocol (SSL) is the way to send information securely from a client to server and vice-versa over the internet.For a SSL connection to happen between a client (web application running i...
📚 Read more at Javarevisited🔎 Find similar documents

SSL
Secure Socket Layer (SSL) is a cryptographic protocol for securing computer networks. Note : SSL was deprecated in 1999 and renamed Transport Layer Security (TLS) by the Internet Engineering Task Forc...
📚 Read more at Codecademy🔎 Find similar documents

— TLS/SSL wrapper for socket objects
ssl — TLS/SSL wrapper for socket objects Source code: Lib/ssl.py This module provides access to Transport Layer Security (often known as “Secure Sockets Layer”) encryption and peer authentication fac...
📚 Read more at The Python Standard Library🔎 Find similar documents

What is SSH?
SSH, or Secure Shell, is a network protocol that allows one computer to securely connect to another computer over an unsecured network, like the internet, by having a shared agreement of how to…
📚 Read more at Level Up Coding🔎 Find similar documents

