API Authentication
𝐃𝐀𝐘 𝟐 : 𝐀𝐏𝐈 𝐀𝐔𝐓𝐇𝐎𝐑𝐈𝐙𝐀𝐓𝐈𝐎𝐍
𝐀𝐏𝐈 𝐀𝐔𝐓𝐇𝐎𝐑𝐈𝐙𝐀𝐓𝐈𝐎𝐍API authorization is a crucial part of communication because it plays a critical role in ensuring the security and integrity of the data exchanged between the client a...
📚 Read more at Javarevisited🔎 Find similar documents

API Authentication with Tokens
In this article I'm going to show you a few common patterns for client authentication based on tokens, and how can they be implemented in a Python API back end. This method of authentication works…
📚 Read more at Miguek Grinberg Blog🔎 Find similar documents

API Security Essentials: Comprehensive Practices to Safeguard Your Data Exchange
Introduction In today’s interconnected world, where data exchange between applications and services is commonplace, the security of APIs (Application Programming Interfaces) is paramount. APIs serve a...
📚 Read more at Level Up Coding🔎 Find similar documents

Auth Schemes of REST API
The user’s data is the underlying currency that is driving the API economy. Like any currency, you need to handle it with care and transport it with caution to prevent theft. Different devices and…
📚 Read more at Towards Data Science🔎 Find similar documents
API Authentication with Laravel + JWT
Authentication is a basic feature of most services on the internet. We want to be able to restrict who has access to what, and to do it in the most convenient and secure way possible. This article…
📚 Read more at Level Up Coding🔎 Find similar documents

API Authentication Explained: API Keys, JWT, and OAuth (Without the Boring Jargon)
From every time you check your bank balance, send a message over WhatsApp, or get directions using Google Maps, APIs are doing the unseen work in the background. However, before it provides that sweet...
📚 Read more at Javarevisited🔎 Find similar documents
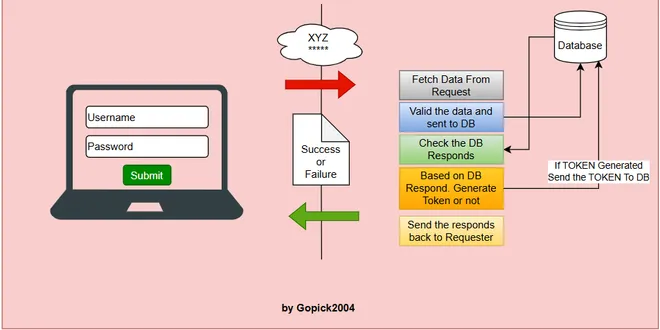
Building a Simple Login API with Spring Boot: My Step-by-Step Guide
Not a member read it here What Is a Login API? A login API is a service that accepts user credentials — like a username and password — and validates them. If the credentials are correct, the API retur...
📚 Read more at Javarevisited🔎 Find similar documents
Creating Secure API’s with EasyAuth & FastAPI
Currently the API is accessible and usable by anyone with a network connection that can reach the server: Instead of re-creating users, group, roles, & permission, centralize into a single auth…
📚 Read more at Analytics Vidhya🔎 Find similar documents

Spring Boot — Securing API with basic authentication
Spring Boot — Securing API with basic authentication Introduction : In today’s article, we will discuss what is basic authentication and securing spring boot rest APIs using basic authentication. Pre...
📚 Read more at Javarevisited🔎 Find similar documents

Secure Your Azure Functions Endpoints(Open API) with Basic Authentication (.NET)
Introduction This guide explores integrating OpenAPI, the modern specification for APIs, to streamline the process. While basic authentication offers a simple approach, keep in mind it might not be su...
📚 Read more at Level Up Coding🔎 Find similar documents

Authenticate with Alpaca API
The {alpacar} package for R is a wrapper around the Alpaca API. API documentation can be found here. In this introductory post I show how to install and load the package, then authenticate with the AP...
📚 Read more at R-bloggers🔎 Find similar documents
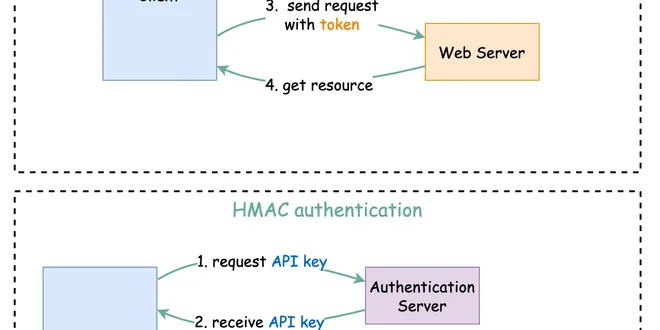
How to design a secure web API access for your website?
How to design secure web API access for your website? When we open web API access to users, we need to make sure each API call is authenticated. This means the user must be who they claim to be. In th...
📚 Read more at ByteByteGo Newsletter🔎 Find similar documents

