Web Security

Web Application Security
Web applications can be attacked many ways by malicious actors. Learn more on Full Stack Python.
📚 Read more at Full Stack Python🔎 Find similar documents

Security
No security is perfect, but there’s a number of important restrictions built into MashProxy and SearchMash. The security in MashProxy is based around the Java applet being digitally signed. This signa...
📚 Read more at Pete Warden's blog🔎 Find similar documents

Security Intro
Security Intro There are many ways to handle security, authentication and authorization. And it normally is a complex and "difficult" topic. In many frameworks and systems just handling security and ...
📚 Read more at FastAPI Documentation🔎 Find similar documents
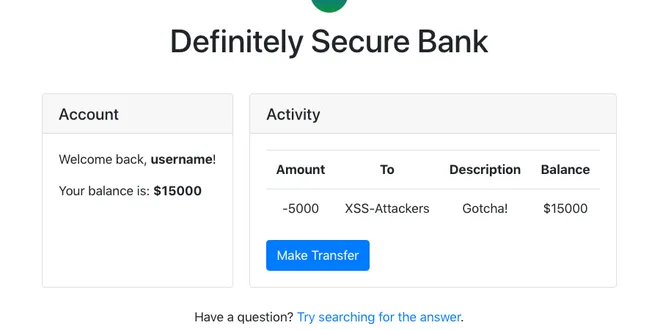
Web Security 101: Cross-Site Scripting (XSS) Attacks
A hands-on beginner's guide to what XSS attacks are and how to prevent them.
📚 Read more at victorzhou.com🔎 Find similar documents
Web Security: What is a JWT?
JSON Web Tokens (JWTs) are a type of security token that uses JSON to encode information about an entity. They are used to authorize requests and access sensitive data. In this blog post, we will…
📚 Read more at Level Up Coding🔎 Find similar documents

Web Security: What Is XSS?
A Cross-Site Scripting attack, or XSS for short, is a type of cyber attack that uses malicious scripts to inject into webpages. These… Continue reading on Level Up Coding
📚 Read more at Level Up Coding🔎 Find similar documents

Enabling HTTPS and securing your website using Let's Encrypt
A non-secure website has HTTP at starting of the URL. Whereas websites starting with HTTPS are the secure ones, the ‘s’ stands for secure. You must have seen sometimes your browser gives notification…...
📚 Read more at Analytics Vidhya🔎 Find similar documents

OWASP: Introduction to Web Application Security
OWASP | Security | Django| Web Development
📚 Read more at Level Up Coding🔎 Find similar documents

Five short links – Security edition
Photo by Darwin Bell Now I'm looking at handling more sensitive customer data I have an obligation to do everything I can to secure my server and code. Here's five resources I've found helpful: Nikto ...
📚 Read more at Pete Warden's blog🔎 Find similar documents

Security Considerations
Security Considerations Web applications usually face all kinds of security problems and it’s very hard to get everything right. Flask tries to solve a few of these things for you, but there are a cou...
📚 Read more at Flask User's Guide🔎 Find similar documents

Security Considerations
Security Considerations Web applications usually face all kinds of security problems and it’s very hard to get everything right. Flask tries to solve a few of these things for you, but there are a cou...
📚 Read more at Flask User's Guide🔎 Find similar documents
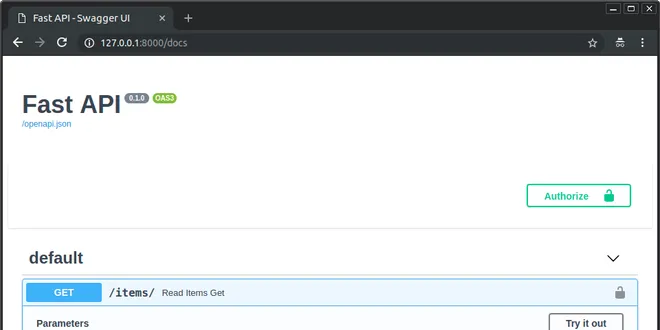
Security - First Steps
Security - First Steps Let's imagine that you have your backend API in some domain. And you have a frontend in another domain or in a different path of the same domain (or in a mobile application). A...
📚 Read more at FastAPI Documentation🔎 Find similar documents


